https://www.wordfence.com/blog/2019/01/analyzing-a-week-of-blocked-attacks/
If you’ve never taken a few minutes to look at the information available in the Wordfence Live Traffic feature, I strongly recommend it. It gives you a detailed look at what attackers are trying to do to break into your site, and how Wordfence is blocking them.
For today’s post we analyzed all of the blocked attacks on Defiant.com for a week. In order to see them in Live Traffic, I simply selected “Blocked by Firewall” from the “filter traffic” drop-down above the data table.
What Attackers Were Up To
For the week there were a total of 223 attacks blocked. I was excited to see that all of them were blocked by the Wordfence real-time IP blacklist. We are used to seeing really high percentages blocked by our blacklist – usually in the high 90s. The real-time IP blacklist is a Premium feature that blocks all requests from IPs that are actively attacking WordPress sites.
Attacks originated from 14 unique IP addresses from around the world. Of the countries represented, Germany was the origin for the most attacks at 85. India was second with 61 and France was third with 45. Other countries represented were Ukraine, South Africa, China, Italy and the United Kingdom.
Next we’ll break down what they were trying to do to break in.
Reconnaissance
Five of the IPs appeared to just be performing reconnaissance, as they were simply requesting our home page or some other page on the site. They were likely just checking to see if the site was up and responding to their requests. Since all of the IPs were on the Wordfence real-time IP blacklist, their requests were blocked and they moved on after a couple of blocked page requests.
Author Enumeration
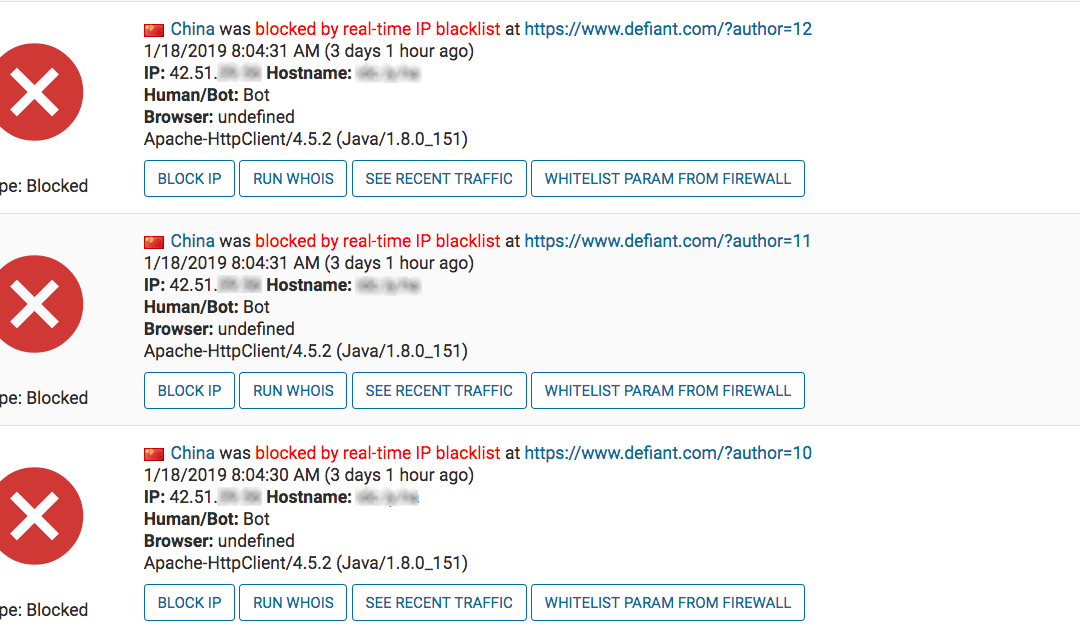
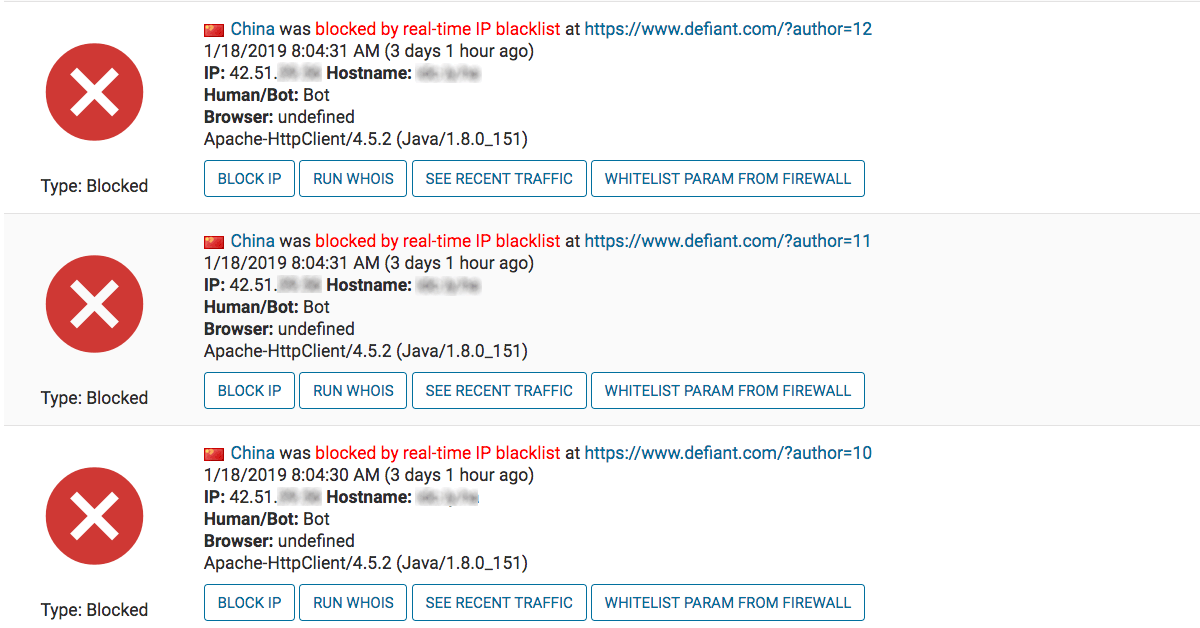
A Chinese IP attempted to retrieve a list of author usernames for the site. Since the authors of posts are very often also administrators, this information can significantly improve the odds of success for a brute force password guessing attack. The attacks all look like the following:
https://www.defiant.com/?author=1
The attacker worked through fifteen author numbers before giving up and moving on. In the Wordfence “Brute Force Protection” settings, look for the following option to enable this feature:
“Prevent discovery of usernames through ‘/?author=N’ scans, the oEmbed API, and the WordPress REST API”
Once you enable this, Wordfence will block these scans. This option is enabled by default and is available for both free and premium users.
We have blocked 382,131 attacks from that IP in the last 7 days across all of our customers. It seems quite likely that had the attempt to retrieve usernames been successful, attempts to log in using lists of common passwords would have followed.
Login Attempts Via XML-RPC
Sixty Three of the blocked attacks were attempts to log in to the site via the XML-RPC interface, which is an API developers can use to communicate with WordPress sites. We see a high percentage of brute force password guessing attempts hit this interface.
In our case we saw a single IP from Chennai, India attempt 61 login attempts in the period of just over an hour. Two other IPs, one in Hong Kong and another in Italy, made just one attempt each. They most likely moved on because they were blocked.
Login Attempts Via wp-login.php
We had just one IP attempt to login via the interface you use to login your site. The first attempt to login was followed immediately by an attempt to access our home page. The script was most likely checking to see if they were only being blocked from accessing the login page or the entire site. A second attempt following the same pattern occurred just two minutes later. We didn’t see additional attempts from that IP. I assume the attacker’s bot is programmed to move on if it’s blocked twice in a row.
A French IP Probes for Opportunities
A single French IP sent 43 requests in a 33 second burst. The first was a simple home page request, which I assume was an attempt to verify the site was up and accepting requests. Surprisingly the attack continued despite being consistently blocked by the Wordfence firewall. The following are a few examples of what the attacker was up to.
One request was checking for the existence of a known malicious file, commonly used by attackers to upload files to hacked websites. The request looks like this:
https://www.defiant.com/wp-upload-class.php
Another interesting request was looking for opportunities to exploit fresh WordPress installs, which we wrote about in July of 2017. Here’s what the request looks like:
https://www.defiant.com/wp-admin/setup-config.php?step=1
We also saw two attempts to find a copy of searchreplacedb2.php laying around. In July of 2017 we wrote about how hackers use the searchreplacedb2.php script to make malicious database changes. Here’s an example request:
https://www.defiant.com/searchreplacedb2.php
A German IP Probes for Opportunities
A single IP from Hirschfield, Germany attacked our site 85 times in just under two minutes. Most of the attacks were repeats of what we saw from the French IP. So it’s possible that it was a different bot at work for the same attacker. However, this IP also attempted to exploit a number of known theme and plugin vulnerabilities.
All of these attempts to exploit known vulnerabilities were trying to download the wp-config.php file, which is a WordPress file that includes the database credentials for the site. If successful, these attacks would give the attacker an easy route to obtaining administrative control of target website.
In one example, the attacker is attempting to exploit an arbitrary file download vulnerability in the “Epic” theme that was disclosed way back in 2014.
https://www.defiant.com/wp-content/themes/epic/includes/download.php?file=wp-config.php
In another, the attacker is trying to exploit a different arbitrary file download vulnerability – this time in the WP Hide & Security Enhancer plugin. The vulnerability was disclosed less than six months ago.
https://www.defiant.com/wp-content/plugins/wp-hide-security-enhancer/router/file-process.php?action=style-clean&file_path=%2Fwp-config.php
It’s important to note that we are not running any of the themes or plugins this attacker is attempting to exploit on Defiant.com. Many of the attacks on WordPress sites are what we often refer to as “spray and pray” attacks, where the attacker simply tries hundreds or thousands of exploit attempts hoping to get lucky. It’s likely that attack volumes are lower for Defiant.com because it’s protected by the Wordfence real-time IP blacklist. Like you, attackers don’t want to waste resources. If all of their attacks are being blocked they will move on to an easier target.
Conclusion
As you know, WordPress sites are under constant attack. There are many attackers, all of whom deploy different tactics. The free version of Wordfence includes protection for all of the attacks outlined above. For even better peace of mind, and likely lower attack volumes, consider upgrading to Wordfence Premium. For only $8.25 per month (billed annually) you can put the Wordfence real-time IP blacklist to work protecting your site around the clock.
The post Analyzing a Week of Blocked Attacks appeared first on Wordfence.
Source: Security Feed