https://www.wpwhitesecurity.com/dns-tools-queries-wordpress-users-administrators/
When you buy a new domain for your WordPress site you have to configure the name servers and other DNS records. Configuring your the Domain Name System (DNS) for your domain is a simple process, and it becomes even easier when you understand how DNS works, what are Domains, Registrars and DNS records.
However, a small mistake in the DNS configuration can lead to big problems – people won’t be able to access your website or send you emails. This article explains how you can use nslookup, dig and other DNS tools to test your DNS setup.
Nslookup and Dig DNS Tools
Both Nslookup and Dig are command line tools found on many operating systems. These tools are used to send queries to DNS servers. Nslookup is more popular with Windows users and Dig is more popular with Mac OS and Linux users. Both’s queries and commands are similar.
In this article we use both Nslookup and Dig to explain how you can use them to check the configured records on a DNS server. We also explain how to check the properties of DNS records, such as TTL. And last but not least, we will also see how to check the propagation of a DNS record and how to do other troubleshooting.
Querying a DNS Server with Dig
The most basic DNS query you can send to a DNS server is to resolve a domain name into an IP address (A record). By default both the Dig and Nslookup tools query A records, so just type the below in the command line to get the answer:
- Linux / Mac: dig www.wpsecurityauditlog.com
- Linux / Windows: nslookup www.wpsecurityauditlog.com
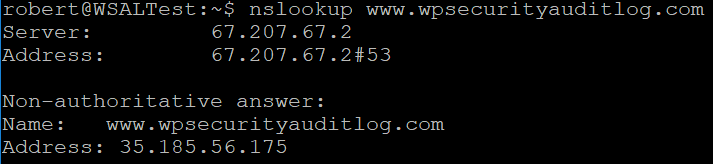
Below is a screenshot of the nslookup command and the response from the server:
Here is a breakdown of the response:
- Server:67.207.67.2 is the IP address of the DNS server we queried and sent a response.
- Address:67.207.67.2#53 is the IP address and port number of the DNS service.
- Name: www.wpsecurityauditlog.com is the domain name we queried.
- Address: 35.185.56.175 is the IP address where the domain www.wpsecurityauditlog.com is hosting. This is the record we are looking for.
Authoritative & Non-Authoritative Answers from the DNS Server
Did you notice the text non-authoritative answer: in the DNS server response? That means that the server you queried is not the authoritative name server of the domain wpsecurityauditlog.com. So the answer we received is a cached or forwarded response.
To get a response from the authoritative server you have to find the name servers (NS records) of the domain and query them directly. We’ll do this in the below example.
DNS Tools Usage Examples
Finding the Name Servers of a Domain
The name servers of a domain are the servers that hold the DNS zone of a domain (the main authority for that domain). These are the servers you specify when registering a new domain, as explained in the DNS guide for WordPress site owners.
To find the name servers of a domain use the following command:dig [domain_name] NS. NS is the type of DNS record we want to know. So to find the NS (name server) records of the domain wpsecurityauditlog.com, the command should be:
dig www.wpsecurityauditlog.com NS
Below is a screenshot in which the request and the important sections from the answer are highlighted:
- This is the command.
- As part of the response you can see that we have sent one query (QUERY:1) and got four answers (ANSWER: 4).
- This is list of the four name servers for the domain wpsecurityauditlog.com. In this section you can also see the Time to Live (TTL) value of every record, which is 86112.
- Technical details of the query, such as how long it took the server to respond, when was it sent, the size of the message etc.
Querying a Different DNS Server
By default the Dig or Nslookup tool sends the query to the DNS server configured on your device’s network interface. Typically this is the DNS server of an ISP, a web host, or of the network you are connected to. Therefore if you want an authoritative answer about a particular record or FQDN you have to query the name server directly. To do this use the following command format:
dig @[server] [domain]
Since now we know the name servers of the domain wpsecurityauditlog.com, we can query one of them directly. In this case we are querying 162.88.61.47, which is the IP address of the ns1cvw.name.com name server. We want the server to resolve the IP address of the FQDN www.wpsecurityauditlog.com. The command is:
dig @162.88.61.47 www.wpsecurityauditlog.com
Here is the response from the server:
- The dig command.
- This is the answer from the server. The FQDN www.wpsecurityauditlog.com resolves to the IP address 35.185.56.175.
Using DNS Tools to Find a Domain’s Mail Servers
When you send an email to support@wpsecurityauditlog.com your mail server sends DNS requests to find the IP address of the wpsecurityauditlog.com domain mail servers. Mail server records on DNS are MX records, also known as Mail Exchanger records. To find the MX records of a domain use the following command format:
dig [domain] [MX]
Below is the response from the DNS server for the dig wpsecurityauditlog.com MX command:
- The Dig tool command.
- The DNS server’s answer.
From the answer we can see that the domain wpsecurityauditlog.com has five mail servers. The number in front of every mail server record is the server’s priority. The lower the number is, the higher the priority. This means that when you send an email to this domain, first your mail servers try to connect to aspmx.l.google.com because it has a priority of 1. If for some reason it is unavailable, then the servers try to connect to the next server, in this case with priority 5.
Other Uses for DNS Tools
The Dig and Nslookup DNS tools can be used to query any DNS server for any type of record. For example you can also use these tools to retrieve the TXT records of a domain, which are typically used by SPF and other frameworks. Dig also the any switch. When used it downloads all the records for a particular domain.
Therefore if you want to learn more about DNS and the different types of records try getting the records for google.com or wikipedia.org.
Checking DNS Propagation
To minimize traffic and requests between servers, DNS servers cache DNS records for the time specified in the Time to Live (TTL) value. TTL is specified in seconds for every DNS record and it is like an expire date.
The higher the TTL value of a DNS record the longer it will take for a change to propagate, because the DNS servers cache the record for much longer. On the other hand, a low TTL value means that a DNS record change will be propagated very quickly. However a low TTL value also means an increase in the number of DNS resolution requests.
You should set a high TTL value for DNS records, like 86,400 seconds (24 hours). Only use lower values, something like 3,600 seconds (1 hour) when you are planning a DNS record change. As long as you lower the TTL a few days or weeks before the change, the change should be propagated in a respectable time.
You can use the free online tool What’s My DNS to check if a DNS record change has been propagated. To run a test simply type in the record and configure the expected results by clicking on the cogwheel.
The post DNS Tools & Queries For WordPress Users & Administrators appeared first on WP White Security.
Source: Security Feed