https://www.wpwhitesecurity.com/how-does-vpn-work/
In recent years Virtual Private Networks (VPN) have become increasingly popular with both business and home users. And it’s reasonable to assert that this interest in VPN solutions has been amplified by the various security and privacy issues that have been highlighted in the mass media.
Yet many people, even those who use VPNs on a regular basis don’t know how the technology works. So in this article, we’re going to take you through everything you need to know about how VPNs operate.
The Encryption Key
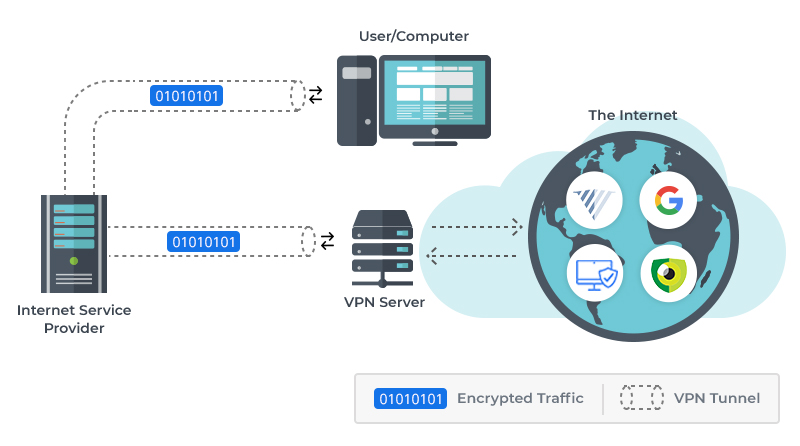
The central process with any VPN is the encryption of data. VPN software encrypts all the information sent out by your computer. This means that your Internet service provider, and the wider Internet, cannot intercept the traffic that you are transmitting over the worldwide web.
Encryption works by applying a secret code to the data in order to transform it in an undecipherable form. The information can then only be decrypted by a system that also has the key used to encrypt the data (pre-shared secret key), meaning that VPN networks are extremely difficult to crack. Most modern VPN systems, including NordVPN now offer AES-256 encryption. This level of encryption is practically impossible to breakdown. The security keys used to encrypt the data are hugely complex and have been the subject of several pieces of doctoral research.
Transmission of Data Over VPN
Once the data is encrypted on your computer it is sent through the virtual private network tunnel to the server that your VPN provider operates. This is part of the process of protecting your privacy and anonymity – all data between your computer and VPN server is encrypted.
The VPN server then transmits the data to whichever online destination / website it was intended to. The data between the VPN server and the target website is not encrypted, however to the online destination the traffic is originating from the VPN server and not your computer, thus disguising your computer and your location.
The Purpose Of A VPN Service
The three main benefits of a VPN service are:
- Extending the private network over the internet (mostly for business use)
- the encryption of transmitted data
- the hiding of your physical location.
The VPN server acts as a middleman, which effectively connects to the Internet on your behalf. Note that if you login to a website which keeps a record of all changes in a WordPress audit log (audit trail), the site owner will still be able to see that you logged in and what changes you have done. However the source IP address from where you are logging in will be that of the VPN server.
Legal Limitations
Although VPNs have become commonplace, there are legal and policy limitations affecting what can be achieved with the technology. While VPNs enhance privacy considerably, the laws of the nation in which the VPN service is located can have a significant impact on the way that it operates.
The first field to which legal limitations apply are the protocols used by the VPN service. Protocols determine how the data is transmitted between your computer and the VPN server. The most common protocols are PPTP, IPsec over L2TP, SSTP, IKEV2, SSL and OpenVPN.
The most sophisticated and sought-after VPN services will utilize as many of these protocols as possible, but there can be some legal restrictions depending on the territories involved. This is a controversial area, but some countries do not allow certain protocols, meaning that they cannot be offered by VPN services.
In some nations, the legislation might also force VPN companies to share user activity records. And this picture is further clouded by the international agreements in place which see countries sharing information in such cases. Nonetheless, it is possible to find VPN services established in countries that don’t have any such international agreement in place.
Explanation Of The Different Protocols Used In VPN
Let’s break down each of these protocols:
PPTP is an abbreviation of Point-To-Point Tunneling Protocol. It is one of the oldest protocols that remains in use with the contemporary Internet. It was originally designed by Microsoft and is part of the Windows operating system. Although this protocol is easy to implement, PPTP is criticized in some quarters for offering poor standards of security. It is certainly advisable to avoid any provider which only offers this protocol.
L2TP: sometimes also referred to as IPsec refers to Layer 2 Tunneling Protocol. This protocol was originally based on the PPTP and Cisco’s L2F protocols. It uses keys in order to establish a secure connection but has been criticized for unsafe execution. Some reports suggest that it is possible to breakdown L2TP.
SSTP (Secure Socket Tunneling Protocol) is another protocol from Microsoft, which uses SSL/TLS encryption. This protocol takes advantage of symmetric-key cryptography, which is considered a particularly secure solution. It enables only the two parties involved in a data transfer to decode information. SSTP has established itself as a major technology in this niche, along with IKEv2 (Internet Key Exchange, Version 2), which is another Microsoft product.
OpenVPN is often seen as the best available protocol, not only because of the sophisticated SSL/TLS but also because thousands of the best minds in technology contribute to it, since it is an open source project. This means that OpenVPN is continually being improved, leading to it generally being regarded as the most versatile and secure protocol.
Tunneling In VPNs
The final important aspect of VPN technology’s security is its ability to segregate the packets of data from one another. When information is transmitted between computers across the Internet, requests and responses are broken down into a series of packets. This is where the concept behind the ‘packet’ sniffing software emanates from.
In order to segregate your traffic from the rest of the public traffic, and to prevent any nefarious individuals from getting their hands on information, VPNs use a tunneling mechanism. This means that the data between your computer and the VPN server is actually sent via a virtual tunnel. This process of layering packets is frequently referred to as encapsulation.
Protect Your Privacy With VPN
VPNs use a variety of techniques to ensure that your privacy and anonymity can be maintained, and the sophisticated methods involved mean that they are extremely difficult to crack and break down.
So make it a point that whenever you are working from public places, and using public WiFi’s in cafes, hotels and similar places you always use a VPN service to access the internet. And always use a strong password for your WordPress sites and any other service you use, because VPNs, HTTPS, 2-Factor Authentication and other security mechanisms won’t work to their full potential without a strong password.
The post How Does A VPN Work? appeared first on WP White Security.
Source: Security Feed