https://blog.threatpress.com/pharma-spam-identify-hacked-website/
Pharma Spam or Pharma Hack is a type of SEO spam used by hackers to improve the SEO rank of websites selling pharmaceutical products like Viagra, Cialis, Xanax, Valium, and Celebrex. Hacked Website Report 2017 found that 44% of all malware attacks included the creation of SEO spam campaigns on the targeted site. This kind of attacks involves the addition of new pages or alteration of existing pages to add links for SEO purposes.
In this guide, we’ll explain how pharma spam works then offer some tips for checking if you have any pharma spam on your website. Finally, we’ll share a few tips for securing your website against this kind of attack.
How do Pharma Spam attacks work?
Pharma spam is a form of Black Hat SEO called spamdexing. Spamdexing uses a variety of techniques to get links placed onto other people’s websites. These links will point to other hacked websites with more links or directly to the hacker’s “money sites” — which are the sites that they want to rank-up in search engines.
Spamdexing is an effective technique because search engines use the number of links coming into a website to help determine where it ranks in search engine results. If a hacker can use exploits or spamming techniques to obtain links on thousands of websites, their money sites will rank higher and make more money.

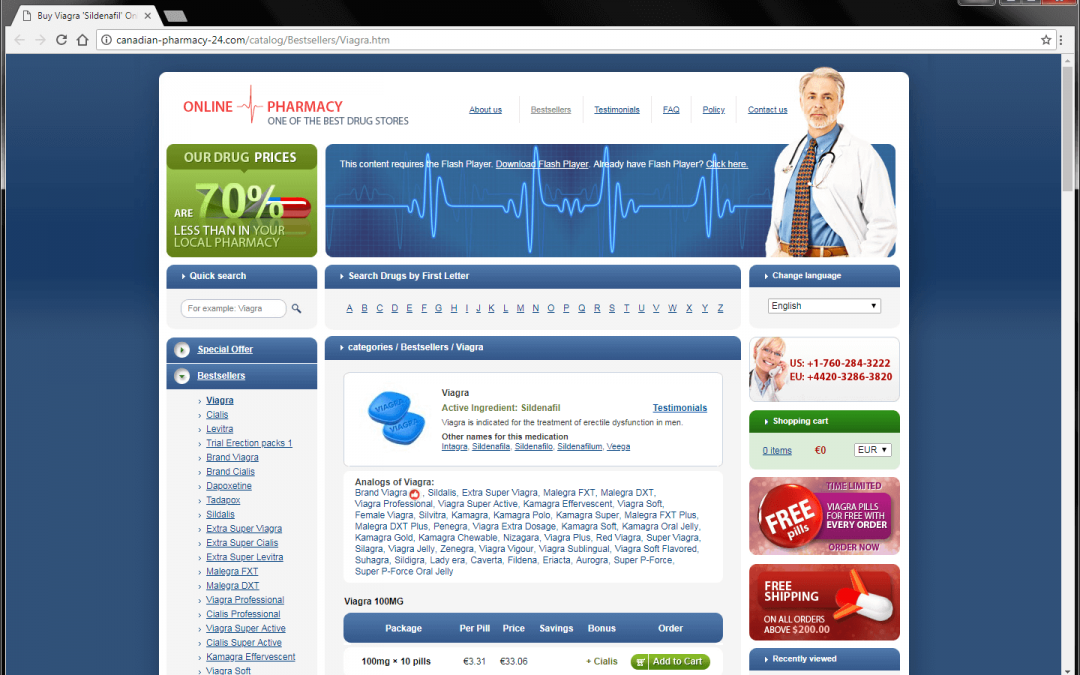
Pharma spammers may also place entire pages of spam on other people’s websites (as shown below). These pages are fully functional sales pages that send clients to payment gateways to purchase products.

There are three stages of most pharma spam attacks on WordPress websites.
Step 1: The hacker will use a backdoor to gain remote access to your site
The hacker must find a way to upload a malicious file to your website before they can run their spam scripts. They will usually start by looking for sites that are running an outdated version of WordPress or which are running a plugin that can be exploited. Sometimes, hackers will target a specific hosting company that is known to have lax security on their servers.
Once the backdoor is installed, the hacker may or may not use it immediately — it depends on the status of their black hat SEO campaigns.The most common locations for this kind of backdoor script are inside wp-content/uploads/.*php (with a random PHP name file), wp-includes/images/smilies/icon_smile_old.php.xl, wp-includes/wp-db-class.php and wp-includes/images/wp-img.php.
The contents of this file usually include a long encoded string that uses the eval() function to run. The string will look like a jumbled series of letters and numbers.

The hacker will run this file remotely to scrape your database details from wp-config.php. The file will then act as a remote shell, giving the hacker all kinds of information about the server. Once the hacker has the database login details from wp-config.php, they can modify and add pages as they see fit.
Locating this backdoor file and removing it is usually the first step to perform when removing pharma spam from a website.
Step 2: The backdoor adds files to plugin folders
The backdoor will then add more files to your WordPress installation. These files will help the hacker create and manage their pharma spam attacks.
These files will usually be installed in a plugin directory. They will often be named in a way that resembles the plugin directory in which they are located. For example, if they have been installed in the Jetpack plugin directory, they might be named wp-jetpack.php, db-jetpack.php, ext-jetpack.php. In some cases, they might use hidden files or image files to store some types of data.
The easiest way to ensure that your plugin directory is clean of malicious folders is to reinstall them from a reputable source.
Step 3: The backdoor modifies the database
Finally, the hacker will make some changes to your database so they can add their pharma spam. They will often make changes to the wp_options table, adding records to help their software run.
Pharma spam malware adds rows in the wp-options table like “class_generic_support”, “widget_generic_support”, ”wp_check_hash”, “fwp”, and “ftp_credentials”. You should delete these records from your database if they are present.
The hacker’s backdoor may also make changes to the users registered on your website or will even add new users with administrator permissions. You will have to check the registered users, their email addresses, and reset all passwords to address this risk.
How does Pharma Spam affect your website
Unfortunately, having pharma spam on your website carries some negative consequences including:
- Forcing your website to rank lower – when Google sees that you have dozens of spammy outbound links on your website’s pages, it may reduce your search engine rankings.
- Your website may be blacklisted – spammy links that go to low-quality spam sites are against search engine guidelines. If your website accumulates enough of these links, it may be blacklisted from some search engines.
- If your site is compromised to pharma spam it might have other issues – if you have a pharma spam problem, it is highly likely that you also have some other forms of malware present on your website. This might include malicious redirects and forced software downloads.
Checking if you have a Pharma Spam problem
Pharma spam is not always easy to detect. If the spammers have managed to create completely new pages on your domain, you may never see them because you don’t know the URLs.
The first time you will be made aware of their presence may be when you receive a penalty from Google or someone tells you that they have found spam on your website. Some techniques you can use to check if you have pharma spam include:
Search your site using Google
Spammers are very effective at getting their spam pages indexed, so they should be easy to find using Google. Visit google.com and search for “inurl:yoursite.com viagra or cialis”. It will show you all of the pages on your domain that contain the words “Viagra” or “Cialis”. Most pharma spam pages will contain one or both of those words. To make it easier you can try the Advanced Search by Google.
Use a malware scanner on your website
There are any third party scanners will check your website for pharmacy spam or website status against several blacklists like Google Safe Browsing, PhishTank, Malware domain list. You can test your site against several blacklists at once here with ThreatPress SiteScan.
Manually inspect your server
You can also navigate through the folders and files on your server to see if there are any new additions.
Removing Pharma Spam from your website
Pharma spam is notoriously difficult to remove because hackers often use multiple backdoors and insert malicious code in different locations. Use the following steps to ensure the method used by the spammers is permanently deleted:
Track down the backdoor
Start by removing the entry point that the hacker used to compromise your website. As mentioned previously, wp-content/uploads/.*php (with a random PHP name file), wp-includes/images/smilies/icon_smile_old.php.xl, wp-includes/wp-db-class.php and wp-includes/images/wp-img.php are the most likely locations. You could also perform a search by date to see which unusual files may have been added recently.
Delete your plugins
Begin by backing up your plugins. Then, backup any data that these plugins saved to the database — if you really need that data. Then delete them. You can reinstall new copies of each plugin from an official source later on. This will ensure any malicious files added to your plugins directories are gone.
Use a WordPress plugin to scan your files
Install a WordPress security plugin and have it scan your WordPress core files to ensure they are correct. This scanner will spot any malicious code that has been added to your WordPress core files. They may help you locate the backdoor if you did not find it in step 1.
Scan your website with a third party tool
There are many third party tools which will scan your website to identify any spam pages or compromised files. The following services offer free scans for malicious files — Norton Safe Web, Scan My Server.
Use server-side anti-virus software
Ensure the server has up-to-date antivirus software installed. Applications like ClamAV, are very effective at locating potentially malicious files.
Change your passwords and check registered users
You should assume that hacker has gained access to your database. You will need to generate new WordPress salt keys and change your passwords for your FTP accounts, databases (important), WordPress users and hosting accounts. Check that there are no additional users in the system and check all email addresses of users.
Remove the spam pages
Pharma spam attacks usually add pages to your WordPress database. Track down all of these pages and remove them. There may also be additional PHP files throughout your installation.
Reinstall your WordPress files, plugins, and themes
For safety’s sake, it is usually a good idea to replace your WordPress core files with new versions. Some pharma spam attacks store files in the active theme’s directory, so delete and replace your theme’s files also.
Check other websites hosted on the same server (account)
If you have an account on the multisite hosting, we suggest you check out other websites because all websites on the same hosting account could be hacked as well.
Resubmit your website to Google
If Google has detected the pharma spam on your website, your website may already be penalised. Once you have repaired your website, go to Google’s Search Engine Console and using the Remove URLs Feature to eliminate any references that Google has to the infected pages. You will then have to go to Search Traffic > Manual Actions and Request a Review of your website.
Ensuring this kind of attack does not happen again
Here are a few steps you can take to ensure you don’t get hacked for pharma spam again.
- Improve your passwords
- Install WordPress security software
- Install a WordPress theme checking plugin
- Never install plugins or themes from an untrusted source
- Keep WordPress, your themes and your plugins updated
- Ensure your WordPress installation is regularly backed up
- Change to a web host that has better WordPress security
For more articles on WordPress security, please subscribe to the site or follow us on social media.
The post How To Identify That Your Website Hacked for Pharma Spam appeared first on ThreatPress Blog.
Source: Security Feed